Deepfake attacks are no longer a futuristic threat – with 19% more deepfake attacks occurring in the first quarter of 2025 alone than all of 2024,1 it’s clear that they’re already impacting businesses. A recent report found that deepfakes now make up nearly 7% of all fraud attempts, which is a 2,137% jump over the past three years.2
Today’s attackers can use AI to recreate faces, voices, and even subtle behaviors like typing patterns or mouse movements. With tools like these, they’re slipping past traditional verification methods and exposing gaps in how organizations protect access and identities.
In this blog, we’ll explain why traditional approaches to access protection fall short and how Safous offers a safer way to secure your critical systems from this new threat.
Why Are Attackers Targeting Privileged Access?
Cybercriminals aren’t just impersonating users to snoop around your files – they’re looking for your most sensitive systems. Once they get past identity verification, their next target is privileged access: the admin-level controls that let them move laterally through your network, install malware, steal data, or disrupt your operations.
Privileged access gives attackers the keys to your infrastructure. And with AI-generated deepfakes, they don’t need to hack their way in. They can simply log in posing as a trusted employee or vendor and bypass legacy defenses that weren’t built with these sophisticated impersonations in mind.

Traditional Defense Stack: MFA + Agent-Based RPAM
Most businesses have tried to stay ahead by combining multi-factor authentication (MFA) with agent-based Remote Privileged Access Management (RPAM). This strategy makes sense on the surface. MFA adds more verification controls, and RPAM manages who can access high-risk systems.
However, MFA depends on three pillars:
- Something you know (like a password)
- Something you have (such as a security token)
- Something you are (biometric data)
Deepfake technology has turned that last pillar of MFA – something you are – into a new point of weakness. Meanwhile, agent-based RPAM solutions can help organizations secure connections from deepfake attacks, but they also create challenges that are becoming hard to ignore.
Why Agent‑Based RPAM Is No Longer Enough
Agent-based RPAM works by installing software agents on user devices or on target systems. This approach can be effective for combating deepfakes, but it also introduces issues like:
- Performance slowdowns on user devices
- Critical system disruptions when updates or patches go wrong
- Compatibility conflicts across different environments
- Increased operational complexity for in-house IT teams
Ultimately, agent-based RPAM often creates friction and risk that modern businesses no longer need to accept.
Enter Safous: A New, Agentless Approach to RPAM
Safous Privileged Remote Access was built to address these modern challenges head-on. Unlike traditional tools, Safous is agentless – so you don’t need to install software agents on user devices or target systems to protect against identity-based attacks.
What does this mean for your business? It means:
- Employees and contractors can connect securely through browser-based sessions, with no local software to install, no privacy headaches, and no performance drag.
- Servers and OT devices stay untouched and stable without any risk of downtime or operational disruptions.
This agentless approach not only makes RPAM deployments much faster but also reduces costs and helps keep operations running smoothly.

5 Benefits of Safous' Agentless RPAM
Let’s take a closer look at some of the ways Safous can help you stay ahead of deepfake attacks:
1. Just-in-Time (JIT) Access
Safous Privileged Remote Access supports JIT access, which only grants users access when they need it. Once the task is finished, it automatically revokes those privileges, narrowing the window of opportunity for attackers and reinforcing least-privilege access.
2. Passwordless, Cryptographic Authentication
Safous uses cryptographic keys tied to the user’s device, which removes reliance on passwords (which are often the weakest link) and helps prevent risks like phishing, credential stuffing, and deepfake impersonation.
3. Continuous Session-Level Verification
Unlike traditional solutions that verify only at login, Safous continuously monitors user behavior throughout the session. If something unusual happens, like unexpected commands or behavioral anomalies, it can terminate the session immediately.
4. Integrated Protection Layers
Safous includes extra built-in security measures, such as a Web Application Firewall (WAF) to guard against web-based threats and Software Bill of Materials (SBOM) checks to protect against supply chain risks. These layers work together to provide stronger, more complete defense.
5. Unified IAM, PAM, and Zero Trust
Safous rolls Identity and Access Management (IAM), Privileged Access Management (PAM), and zero trust principles into one streamlined solution, making it easier to onboard users, enforce policies, and meet audit requirements without juggling multiple tools.
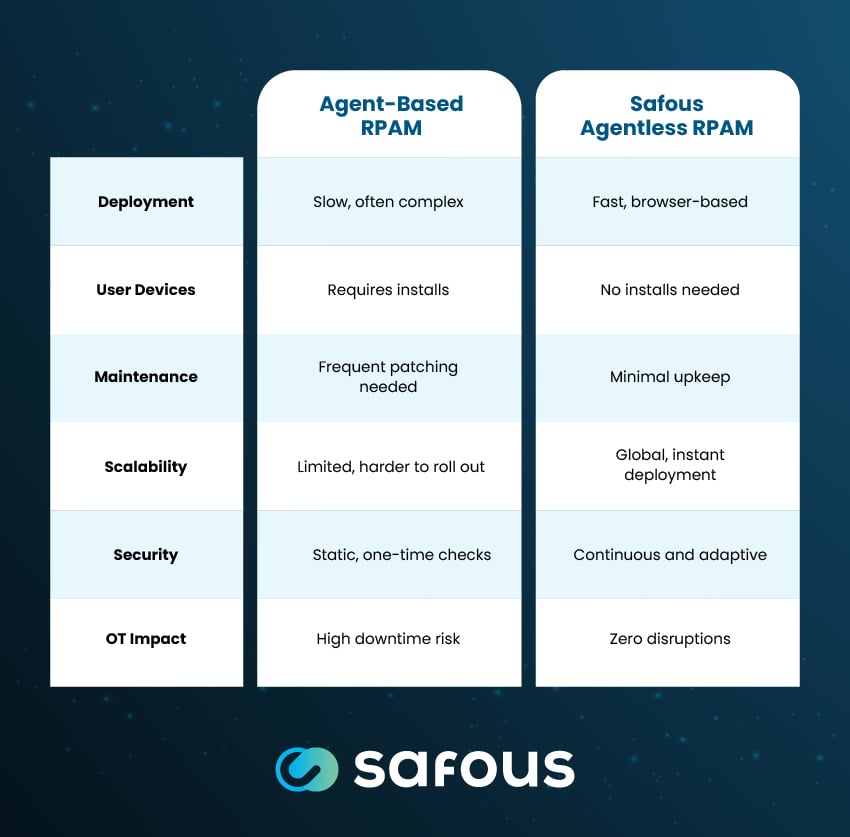
Agent-Based vs. Agentless RPAM: Side-by-Side
If you’ve been using agent-based RPAM, you may wonder how it compares to Safous’ agentless model. Here’s a quick comparison:
|
|
|---|
Get Started With Secure, Agentless RPAM
Deepfake attacks are growing fast, and traditional agent-based RPAM solutions aren’t equipped to keep up. Safous Privileged Remote Access offers a modern, flexible, and agentless way to protect your most critical systems – whether you’re managing IT, OT, IIoT, or cloud environments.
If you’re ready to rethink your approach to RPAM and get ahead of today’s AI-driven threats, we’re here to help. Talk to Safous today to get started.
Sources:
Receive the latest news, events, webcasts and special offers!
Share this
You May Also Like
These Related Stories

Extending Your Legacy Systems’ Lifespan Without Compromising Security

What Is Universal ZTNA?





