USE CASE | THIRD PARTY ACCESSProtect Your Business From Outside Threats
Connecting unmanaged users to your enterprise network can be risky. We’ll help keep your organization safe from malware and data leakage introduced by third parties.
50% of organizations
reported a third-party data breach in 2022.
Watch the video to learn more.
How Safous Prevents Third-Party Access Risks
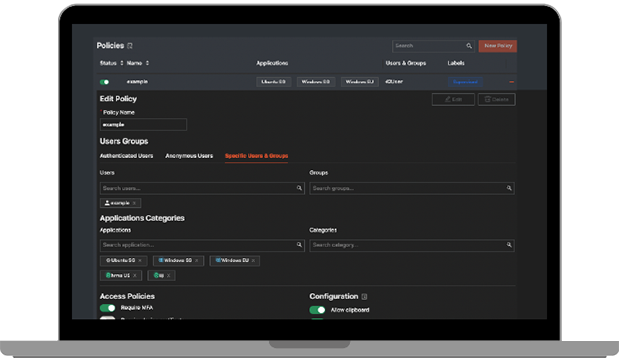
Role-based access control ensures only users who need access to your critical applications will have it.
Policy-based privileges enable admins to control access for both internal users and third parties.
Agentless access management streamlines the process of limiting access for unmanaged users and devices.
Access logging identifies unauthorized activity and determines intent, so you know which third-party users need additional training.
Secure Your Business Against Third-Party Access Risks
Safous ZTA is easy to install and offers a high level of control. Rest easy knowing only authorized users can connect to your critical applications and data.
From Our Blog

From Industry 4.0 to 5.0: Securing Supply Chains in the Human-AI Era
%20Featured%20image_%20Blog%20Zero%20Trust%20vs.%20Legacy%20Security%20Systems_%20What%E2%80%99s%20the%20Right%20Choice_-1.png)
Blog: Zero Trust vs. Legacy Security Systems: What’s the Right Choice?
%20Featured%20image_%20Blog_%20How%20is%20ZTNA%20different%20from%20SASE_.png)


