Supply‑Chain Attacks Are Surging
Rising supply chain threats demand more than outdated VPN security.
Overseas offices create blind spots.
Vendors and partners can become weak links.
Late discovery means costly incidents.
Stronger Protection Starts Here
Comprehensive Scoring
Continuous Monitoring
Expert Analyst Support
How It Works
Our security assessment process is designed to be simple, fast, and non-intrusive.
Step 1
Submit Domains
Specify the domains and subsidiaries you'd like us to target.
Step 2
Automated Scan
We use external OSINT + SecurityScorecard engine to perform non-invasive scans.
Step 3
Analyst Review & Report
You receive your report and portal access within 3–5 business days.
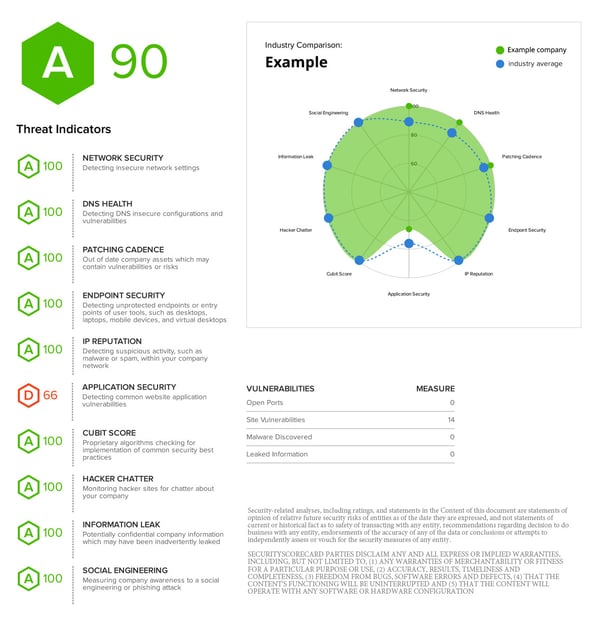
Report Sample
See What Attackers See – Before They Strike
SecurityScorecard Certified
Our Attack Surface Assessment Service leverages the trusted evaluation platform of SecurityScorecard. SecurityScorecard has achieved internationally recognized security certifications, including SOC 2 Type II and ISO 27001, ensuring rigorous data protection and operational security standards. For more details on their certifications, please visit SecurityScorecard’s official compliance page.
Plans
We offer two convenient plans, so you can select the option that works best for your needs.
One‑Time Assessment
Single PDF report
(EN + JP auto‑translation)
- Analyst Meeting
- Professional Translation
Annual Monitoring
12 monthly reports,
portal access, & notifications
- Analyst Meeting
- Professional Translation
Technical Specifications
What does our security assessment involve? Here's what you can expect.
Assets
We'll scan your domains, IP ranges, and cloud assets.
Analysis
Trusted data sources and algorithms are used in analysis.
Methodology
The scans are non‑intrusive, no agents or credentials required.
Privacy
Rest easy with our data handling and privacy assurances.
Assessment Timeline
Gain clear visibility into risks across your supply chain in just a few days.
You submit
your application.
We perform our
scan and analysis.
Your report is
delivered by day 5.
FAQS
We answer the most commonly asked questions about our security assessments below.
No. Our security assessments are completely non-intrusive – we don't require agents, credentials, or direct access to your systems. The scan works from the outside in, using open-source intelligence and trusted data sources to evaluate your security posture without interrupting business operations.
Yes. If you're on the annual monitoring plan, you can submit new subsidiaries, domains, or vendors for assessment at any time during the coverage period. Our team will incorporate them into the next scheduled scan, helping you maintain full visibility as your supply chain evolves.
Reports are available in English and Japanese by default, with professional translation available as an add-on.
Absolutely. On the annual monitoring plan, rescans are performed monthly by default – and we’ll automatically detect improvements or regressions. If you’re on the one-time plan and would like to validate fixes, just let us know and we can schedule an optional follow-up scan.
Ready To Be Secure?
Get the advanced cybersecurity solutions you need to keep your business safer than ever.