Industry 4.0 ushered in the age of large-scale automation, cyber-physical systems, and industrial IoT (IIoT) to drive efficiency and speed in manufacturing operations. It introduced smart factories where machines, sensors, and control systems worked together to streamline production at scale.
Industry 5.0 builds on that foundation. In this new model, human ingenuity works alongside artificial intelligence (AI) to create more flexible, secure, and personalized supply chains. According to the European Commission, Industry 5.0 represents a shift towards a more sustainable and human-centric industry production process1 – enabling collaboration between people and intelligent systems.
But while this new paradigm promises personalization and resilience, it also introduces new security challenges. As AI and automation become more embedded across the supply chain, the number of connected identities, both human and machine, grows. And with that growth comes risk.
How Does Industry 5.0 Differ from Industry 4.0?
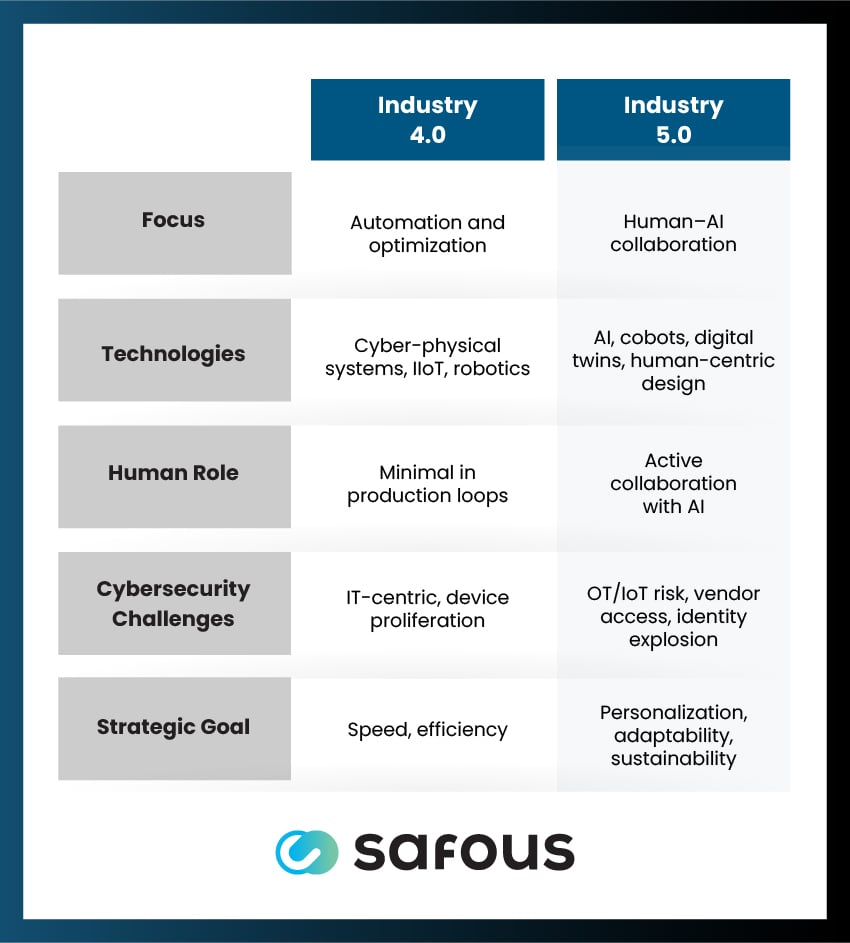
Industry 4.0 was about automation and optimization. Organizations deployed VPNs, static administrative accounts, and perimeter security, all of which were sufficient when IT/OT systems were simpler.
Industry 5.0 is about augmentation. Humans and machines are now co-creating, supported by AI. Traditional security models built around perimeter firewalls, VPNs, and static admin accounts were designed for simpler, more centralized environments. They can’t keep up with new risks like:
- Identity Sprawl: Privileged access is needed across more users, systems, and machines than ever before.
- Machine-to-Machine Connections: IoT gateways and robots exchange data autonomously, often outside the visibility of traditional tools.
- Third-Party Risk: Vendors and partners routinely accessing critical systems are difficult to monitor and control with VPNs alone.
Combating these challenges requires Industry 5.0 environments to shift to identity-based security – where every session is verified, scoped, and logged in real time.
What's the Role of AI in Industry 5.0?
The European Commission is framing Industry 5.0 as human-centric, resilient, and sustainable.1 AI plays a central role in enabling these outcomes by supporting collaboration between people and intelligent systems across the supply chain with:
- Collaborative Robotics (Cobots): AI-powered machines working safely alongside humans.
- Predictive Intelligence: Analytics that anticipate failures and reduce downtime.
- Autonomous Decision-Making: AI orchestrating logistics, quality assurance, and even cybersecurity response.
- Mass Customization: AI enabling bespoke manufacturing at an industrial scale.
- Cyber-Physical Resilience: AI supporting anomaly detection and automated responses.
But with this convergence comes new governance questions. Organizations must define how AI actions are authorized, how those actions are logged, and how they're securing machine identities against compromise.
OT Security: The Blind Spot in Industry 5.0
Industry 5.0 supply chains depend heavily on operational technology (OT) like PLCs, robotics, IoT devices, and SCADA systems. However, these systems weren't designed with cybersecurity in mind, and many can't support modern software agents or regular patching.
OT risks are increasing as a result. Dragos’ 2023 Year in Review revealed that 71% of ransomware attacks targeted the manufacturing sector,2 and Verizon’s 2025 DBIR reported an 89% uptick in confirmed manufacturing data breaches last year.3
In response to these growing threats, governments are reinforcing OT as a focal point:
- CISA’s OT Asset Inventory Guidance positions asset visibility as foundational. 4
- CISA’s Cross-Sector Cybersecurity Performance Goals highlight monitoring as a baseline practice.5
- Singapore’s Cybersecurity Act Amendments extend obligations to OT in Critical Information Infrastructure (CII). 6,7
Recent global attacks on automotive and pharmaceutical supply chains highlight just how fragile OT environments have become.8 And with IBM’s 2024 Cost of a Data Breach Report putting the global average breach cost at $4.88 million,9 securing OT is now a strategic imperative.

What Challenges Do Executives Face?
CISOs and technology leaders managing Industry 5.0 transitions are balancing multiple pressures, including:
- Budget Constraints: Traditional PAM and segmentation projects are capital-intensive.
- Audit Fatigue: Lean teams are burdened by manual compliance reporting.
- Operational Fragility: Downtime in OT systems is unacceptable.
- Vendor Proliferation: Subcontractors and third parties increase access risk for industrial assets.
Conventional VPNs and other legacy tools are falling short when it comes to answering these challenges. In short, security needs to mature – without adding complexity or cost.
How Safous Strengthens Access Security Without Disruptions
Safous was purpose-built to help industrial teams secure remote access and mitigate supply chain risks without re-architecting existing infrastructure. Unlike conventional platforms that require heavy agents or redesigns, Safous enforces prevention and proof to support operational continuity in a browser-based, agentless platform.
It eliminates inbound exposure by allowing outbound-initiated connections from within OT environments (note that certain posture checks require an agent/Internet and may not be available in fully isolated segments), enabling manufacturers to preserve isolation while enforcing tightly controlled, policy-based access. Here's what Safous delivers:
Reduced Attack Surface
Access flows are initiated from inside the OT environment, preserving isolation and reducing attack surface without compromising operational integrity.
Agentless, Browser-Based Security
Single-login access across IT and OT eliminates endpoint overhead, reduces credential fatigue, and accelerates workflows.
Unified Governance Across Identities
Safous centralizes governance for employees, vendors, IoT devices, and AI processes through just-in-time access, MFA, and policy-based controls.
Audit-Ready Transparency
Command-level logging and optional session recording for verifiable audit trails provide evidence in real time, without interfering with production.
Continuous Assurance
Safous consolidates access points and preserves uptime, transforming access control into a driver of agility and resilience.
Enhanced Productivity
Single-login, policy-driven governance reduces friction, accelerates workflows, and improves efficiency.
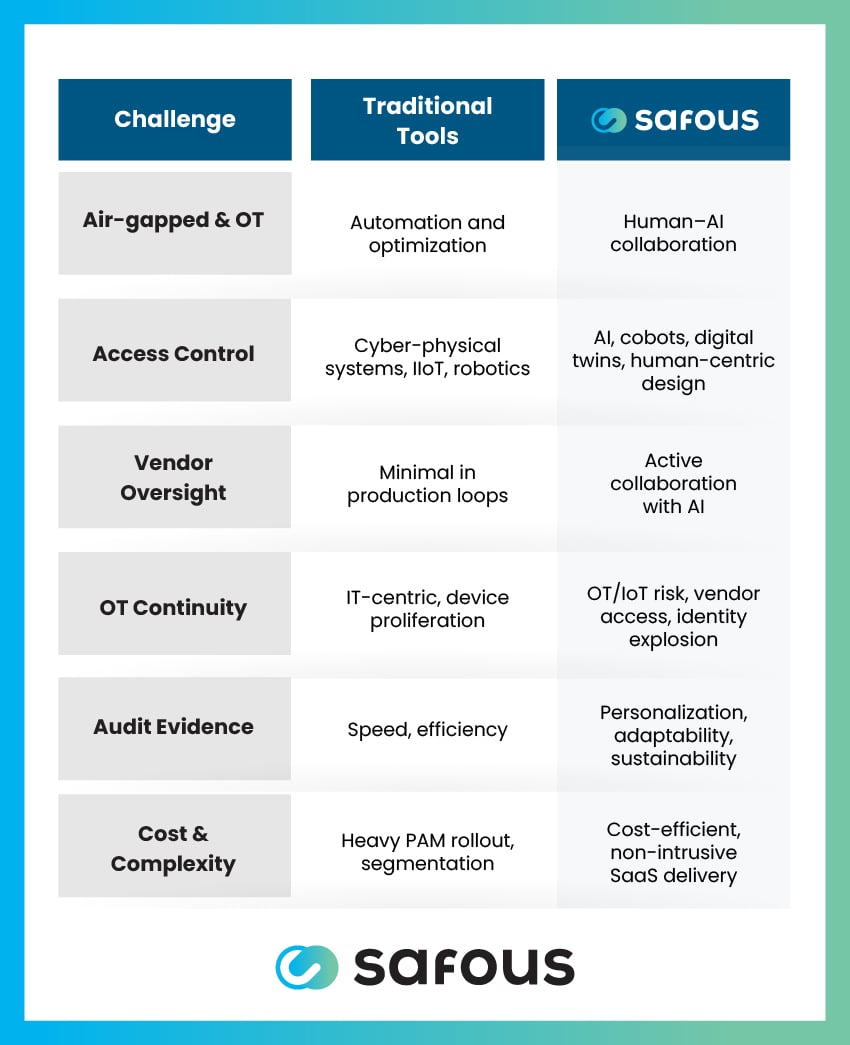
Traditional Access vs. Safous
Safous transforms cybersecurity from an operational safeguard into a board-level differentiator – improving security, efficiency, market trust, and competitive standing in the Industry 5.0 era. Here's how it stacks up against traditional access control solutions:
Embrace Industry 5.0 With Safous
Industry 5.0 brings people and intelligent systems closer than ever before. But as collaboration between humans and machines grows, so does the risk. Staying competitive will mean putting strong security in place without slowing down operations or driving up costs.
Safous makes that possible by delivering Zero Trust access controls, audit-ready evidence, and unified human-machine governance – all without introducing downtime or costly overhauls.
Ready to see how Safous helps manufacturers secure OT access without disrupting operations? Request a demo or talk to an OT Security Specialist today.
Sources:
- https://research-and-innovation.ec.europa.eu/news/all-research-and-innovation-news/industry-50-towards-more-sustainable-resilient-and-human-centric-industry-2021-01-07_en
- https://www.dragos.com/resources/press-release/dragos-ot-cybersecurity-year-in-review-reports-rise-in-geopolitically-driven-attacks-ransomware-and-threat-groups
- https://www.verizon.com/business/resources/infographics/2025-dbir-manufacturing-snapshot.pdf
- https://www.cisa.gov/resources-tools/resources/foundations-ot-cybersecurity-asset-inventory-guidance-owners-and-operators
- https://www.cisa.gov/topics/cybersecurity-best-practices/cross-sector-cybersecurity-performance-goals
- https://sso.agc.gov.sg/Acts-Supp/5-2024/Published/20240216
- https://www.csa.gov.sg/legislation
- https://wisdiam.com/publications/recent-cyber-attacks-manufacturing-industry
- https://www.ibm.com/think/insights/cost-of-a-data-breach-2024-financial-industry
Receive the latest news, events, webcasts and special offers!
Share this
You May Also Like
These Related Stories

Why Human-Approved Access Matters for AI-Automated Operations

Why SASE Doesn’t Meet OT Security Needs, and What to Do Instead



