At its core, an access control matrix is a security model that shows you who is allowed to do what within your systems. Think of it as a master spreadsheet for your security rules. It maps every user against every resource, clearly defining the specific actions they can take at each intersection.
This simple table gives you a powerful, at-a-glance overview of your entire security posture.
Decoding the Digital Rulebook

Picture the security system for a modern office building. You have different people—employees, managers, visitors—who all need access to different rooms, like offices, server rooms, and meeting spaces. An access control matrix works exactly like that building's digital security plan, laying out all the rules in a clear, organised table.
This entire framework is built on three fundamental components that work together to enforce your security policies. Getting to grips with these elements is the first step toward mastering access control.
The Key Players in Access Control
To really understand how an access control matrix works, you have to know its core participants. Each one plays a distinct and essential role every time an access decision is made.
- Subjects: These are the active entities in the system—the "who." A subject could be a person, like a marketing manager, but it could also be a system process running an automated task or even a device trying to connect to the network.
- Objects: These are the passive resources that need protection—the "what." Objects can be anything from a confidential spreadsheet and a customer database to a critical piece of industrial machinery on your factory floor.
- Permissions: These define the specific actions a subject can perform on an object—the "how." Permissions are the verbs of access control: things like read, write, execute, or delete.
By visualising these three components in a grid, the access control matrix gives you a complete and easily auditable map of all access rights in your organisation. For instance, the matrix can spell out that the "Marketing Manager" (subject) has "Read/Write" access (permissions) to the "Campaign Budget" file (object), but only "Read" access to the "Sales Database."
This structured approach eliminates ambiguity. Instead of relying on a patchwork of disconnected rules, the matrix offers a single source of truth for all access control decisions, making it a foundational tool for robust cybersecurity governance.
This clarity isn't just vital for day-to-day operations; it's also crucial for proving compliance with regulatory standards. It provides a clear, documented trail showing that principles like least privilege are being actively enforced across all of your organisation's digital and physical assets.
Peeking Inside: The Core Components of the Matrix
To really get how an access control matrix works, we need to break it down into its three fundamental building blocks. These components work together to create a clear, enforceable security framework. Think of them as the ‘who’, ‘what’, and ‘how’ behind every single access request in your organisation.
Visualising these three elements is the key to unlocking the matrix's power. Each one answers a critical question, and only when all three are defined can you make a truly secure decision. Let's dig into each one with some real-world examples to bring the concept to life.
Subjects: The "Who"
First up, we have the subject. Simply put, a subject is any active entity that requests access to a resource. We often jump to thinking about human users, but this category is actually much broader.
A subject could be:
- A specific user: Like 'Alice', the marketing manager.
- A user group or role: Such as the 'Finance Team' or 'System Administrators'.
- An automated process: A script that needs to hit a database to pull a nightly report.
- A service or application: An API endpoint that needs permission to fetch data from another service.
Basically, if it can kick off an action or make a request, it's a subject. Nailing down your subjects accurately is the first step in building a logical access control matrix.
Objects: The "What"
Next, we have the object. An object is any passive resource in the system that needs to be protected. It’s the ‘what’ that subjects are trying to get their hands on. The scope of objects can be anything from a single file to an entire network segment.
Examples of objects include:
- Digital files: A 'Campaign Budget Spreadsheet' or a 'Client Contact List'.
- Applications: The company's CRM or HR software.
- Databases: The 'Customer Orders' table or the 'Product Inventory' database.
- Physical or Industrial Assets: A server in a data centre, a specific network switch, or even a piece of operational technology (OT) machinery on a factory floor.
Listing every critical object is vital for a complete security overview. This process helps you map out your entire asset inventory and figure out exactly what needs to be locked down.
Permissions: The "How"
Finally, permissions (or access rights) define the specific actions a subject is allowed to perform on an object. They are the verbs that connect subjects and objects, dictating the 'how' of access. Without clear permissions, the relationship between a user and a resource is ambiguous and, frankly, insecure.
For permissions to be effective, they need to be granular. Common examples are:
- Read: The ability to view the contents of a file or database entry.
- Write: The ability to modify or change an object.
- Execute: The permission to run an application or a script.
- Delete: The right to permanently remove an object.
- Append: The ability to add data to a file without changing existing content.
- Own: Full control over an object, including the power to grant permissions to others.
These permissions are the very heart of the principle of least privilege, a cornerstone of modern cybersecurity. By granting only the bare minimum permissions needed for a subject to do its job, you drastically shrink your organisation's attack surface.
The real strength of an access control matrix is how it visualises these relationships in a single, unified view. A cell where a subject's row and an object's column intersect contains the exact permissions granted, leaving no room for guesswork.
This structured approach is particularly crucial in regions with mature cybersecurity frameworks. For instance, Singapore has become a leader in Southeast Asia for adopting robust security standards, using sophisticated access control matrices to protect critical infrastructure in sectors like banking and transportation. This leadership is backed by national strategies that align with global standards and promote secure technology adoption. This level of organised control isn't just a best practice anymore—it's a modern necessity.
Comparing Different Access Control Models
The access control matrix is a fantastic blueprint for mapping out security rules. In the real world, though, that blueprint comes to life through a few different implementation models. Each one tackles the core challenge of managing permissions from a unique angle, with its own set of strengths and weaknesses.
Getting a handle on these models is crucial for understanding how security actually works in the systems you use every day. The big three are Access Control Lists (ACLs), Capability Lists, and the ever-popular Role-Based Access Control (RBAC). Let's break down how each one turns the theoretical matrix into a functional security guard.
This infographic paints a clear picture of the fundamental relationship between subjects, objects, and permissions—the core logic every access control model has to manage.
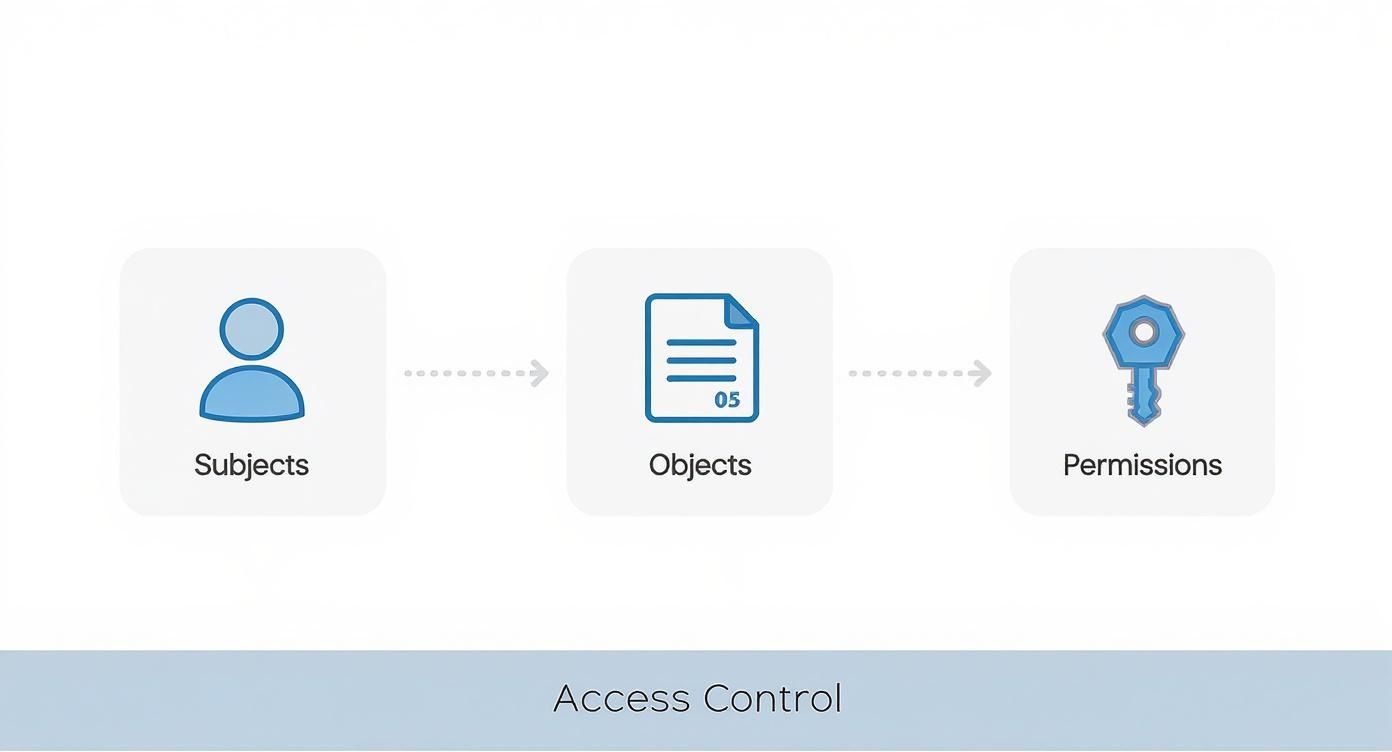
As you can see, the process always kicks off with a subject asking to do something. That request is then checked against the permissions defined for a specific object, which forms the basis for any access decision.
Access Control Lists (ACLs)
Picture an Access Control List (ACL) as a bouncer's guest list, but for a specific room instead of the entire club. Each object—like a file or a folder—has its own list detailing who can get in and what they're allowed to do once they're inside. When a user tries to open a file, the system just glances at that file's ACL to see if their name is on the list and if they have the right permissions.
This is what we call an object-centric approach. The security rules are literally attached to the thing being protected.
- How it relates to the matrix: An ACL is basically a single column from the access control matrix. It tells you everything about one specific object but gives you zero insight into a user's total permissions across the entire system.
- Best for: Simple, small-scale environments where permissions are pretty static, like a basic file server or a network router.
While ACLs are straightforward, they can become a real headache to manage at scale. Just imagine having to update the guest list for hundreds of different rooms every time someone's job changes. It's wildly inefficient and a recipe for mistakes.
Capability Lists
Now, let's flip the ACL model completely on its head. Instead of a guest list attached to each room, what if you gave each person a key ring? Each key is labelled with the room it opens and exactly what it lets you do (e.g., 'unlock and enter' vs. 'unlock and clean'). That key ring is a capability list.
This approach is subject-centric. The permissions are attached to the user or process making the request, not the resource.
A capability acts as an unforgeable ticket or token that grants specific access rights. When a subject presents its capability for a resource, the system verifies the token's validity and grants access without needing to check a central list.
This model decentralises access decisions. The downside? Managing all those "keys" can get complicated. If a key is stolen or needs to be revoked, tracking it down and making sure it can't be used anymore is a serious challenge.
Role-Based Access Control (RBAC)
Role-Based Access Control (RBAC) is, without a doubt, the dominant model in modern business environments. Instead of assigning permissions directly to individuals, RBAC groups users into roles based on their job function—think 'Marketing Manager', 'System Administrator', or 'Sales Representative'. Permissions are then assigned to those roles.
When a new person joins the marketing team, you just assign them the 'Marketing Manager' role. Instantly, they inherit every permission needed for that job, and nobody has to go around editing dozens of individual ACLs. This concept is a cornerstone of modern identity and access management, a topic we dive deeper into in our guide on how IAM, ZTA, and PAM fit together.
RBAC essentially adds a layer of abstraction that makes the whole access control matrix much easier to manage.
- How it works: It creates a middle layer between users and permissions. Users are assigned to roles, and roles are given permissions for objects.
- Best for: Organisations of any size with defined job functions, especially those trying to enforce the principle of least privilege and simplify compliance audits.
By centralising permission management around job roles, RBAC drastically simplifies administration and strengthens your security posture. It ensures consistency and makes it easy to review who has access to what—just look at their role. This model provides the scalability and auditability that ACLs and capability lists just can't offer in complex settings.
To bring it all together, here’s a quick comparison of the three primary access control models. Each has a distinct way of operating and is best suited for different scenarios.
ACL vs Capability Lists vs RBAC
| Model | How It Works | Best For | Pros | Cons |
|---|---|---|---|---|
| ACL (Access Control List) | Each object has a list of subjects and their specific permissions. | Small-scale environments with static permissions (e.g., file systems, firewalls). | Simple to implement for individual resources; granular control per object. | Hard to manage at scale; difficult to get a user-centric view of all permissions. |
| Capability Lists | Each subject holds a list of "keys" or tokens that grant access to objects. | Decentralised systems where subjects need portable permissions. | Efficient access checks; permissions are tied directly to the user/process. | Difficult to revoke access globally; managing and securing tokens can be complex. |
| RBAC (Role-Based Access Control) | Permissions are assigned to roles, and users are assigned to roles. | Most enterprise environments, especially large or complex ones with defined job functions. | Scalable, easy to manage, simplifies audits, and supports the principle of least privilege. | Can be complex to set up initially; might be overkill for very small organisations. |
Ultimately, choosing the right model depends entirely on your organisation's needs. While ACLs and capability lists have their place, RBAC has become the standard for a reason—it offers a powerful combination of security, scalability, and manageability that modern businesses require.
Applying the Matrix in Hybrid Environments
Let's face it: modern organisations rarely live in one neat, tidy environment. Most are juggling a mix of on-premise data centres, various cloud services, and specialised operational technology (OT) that controls real-world physical processes. Trying to apply a consistent access control matrix across this sprawling landscape is a huge challenge.
The real problem is fragmentation. How can you be sure a user’s permissions are the same when they need to grab a file from a local server, query a database in AWS, and then tweak an industrial controller on the factory floor? Without a single, unified strategy, you're left with security silos, clashing policies, and dangerous gaps just waiting for an attacker to find them.
Bridging the IT and OT Divide
One of the toughest hurdles is stretching access control from traditional IT systems into the world of Operational Technology (OT). OT covers the hardware and software that monitors and controls physical gear—think industrial machinery on a manufacturing line or critical infrastructure in the energy sector. Many of these systems were designed decades ago, long before anyone was thinking about modern cybersecurity.
You can't just install a security agent on a 20-year-old programmable logic controller (PLC). Most legacy OT equipment simply lacks built-in security features, making it impossible to enforce granular permissions directly.
This is where the access control matrix shines as an external blueprint. You can enforce its rules by strategically placing security gateways or jump servers in front of these older systems.
- Centralised Identity: All users, from employees to third-party vendors, are managed through a single, central identity provider. This simple step stops the dangerous practice of creating untracked local accounts on OT equipment.
- Gateway Enforcement: When a remote maintenance engineer needs to access a specific machine, they first connect through a secure gateway. That gateway checks the access control matrix to confirm their identity and make sure they have the right permissions (e.g., 'access Machine B', 'maintenance protocol only', 'Tuesday 2-4 PM').
- Session Monitoring: The gateway can then watch and record the entire session, creating a solid audit trail for systems that have no logging capabilities of their own. This clever approach layers modern security controls on top of infrastructure that was never designed to be secure.
The Matrix as a Foundation for Privileged Access Management
In any hybrid setup, some accounts hold the "keys to the kingdom." These privileged accounts, used by system admins and automated services, have the kind of elevated permissions that make them a top target for attackers. Privileged Access Management (PAM) is the entire discipline of locking down, controlling, and monitoring these powerful accounts.
A well-defined access control matrix is the absolute backbone of any effective PAM strategy. It provides the clear, explicit policy that a PAM solution is built to enforce.
By meticulously mapping out exactly which administrator (subject) needs access to which critical server (object) and for what specific reason (permission), the matrix eliminates standing privileges. Access becomes temporary, requested on-demand, and granted only for the duration of the task.
This approach dramatically shrinks your attack surface. If an attacker manages to compromise a standard user account, they can't just hop over to critical systems because there are no permanent privileged pathways left open. Every attempt to gain more privileges is checked against the matrix and logged, triggering immediate alerts for any suspicious activity.
Navigating Regional Security Demands
Getting a robust access control matrix in place isn't just a technical project; it's a direct response to growing security and regulatory pressures around the world. The access control market in Southeast Asia, for example, is growing fast thanks to widespread digitalisation and tougher government oversight.
Singapore's approach, which treats physical and digital security as two sides of the same coin, is a powerful model. The country's smart city projects demand sophisticated access control matrices that govern everything from who can enter a building to who can access the data inside, all driven by advanced biometrics and AI. You can discover more insights about the physical access control market on coherentmarketinsights.com to see how these regional trends are shaping security standards. For any organisation operating in today's hybrid world, this integrated strategy of applying consistent security policies across both physical and digital realms is no longer optional—it's essential.
How the Matrix Powers Zero Trust Security

The old way of thinking about cybersecurity was pretty simple: build a strong wall around your network, and anything inside was considered safe. This "castle-and-moat" approach is dangerously out of touch with reality now. Threats can come from anywhere—including from inside your own walls. This is why the industry has moved to a Zero Trust security model.
Zero Trust works on a simple but powerful idea: never trust, always verify. It starts with the assumption that threats exist both outside and inside your network. Every single request for access has to be authenticated and authorised before it’s granted, no matter where it comes from or who is asking.
But how do you actually enforce this constant verification without grinding everything to a halt? The answer lies in the access control matrix. Think of it as the intelligent rulebook—the engine—that brings a successful Zero Trust architecture to life.
Enforcing Least Privilege Access
One of the foundational pillars of Zero Trust is the principle of least privilege. It’s a straightforward concept: every user, device, and application should only have the absolute bare-minimum permissions needed to do its job. Nothing more, nothing less.
The access control matrix is the perfect tool for making this happen. It lets you define permissions with surgical precision. Instead of giving a user broad access to an entire server, the matrix lets you specify that 'User A' can only 'read' 'File B' between 9 AM and 5 PM on weekdays.
This level of detail is what makes Zero Trust so effective. By using the matrix to get rid of excessive or always-on privileges, you dramatically shrink the potential damage an attacker can do if they manage to compromise an account.
Verifying Every Request Explicitly
A key rule in Zero Trust is to "verify explicitly." This means always authenticating and authorising access based on all the data points you have available—user identity, location, device health, and the specific resource being requested. A static list of permissions just doesn't cut it anymore.
This is where a modern, dynamic access control matrix really shines. It stops being a simple table and becomes a dynamic decision-making tool.
Instead of just asking, "Who are you?", a Zero Trust model powered by an access control matrix asks, "Who are you, what are you trying to access, what device are you using, is that device secure, and are you logging in from an expected location?"
For example, a marketing manager’s role might grant them "read/write" access to the campaign database in the matrix. But if they try to log in from an unmanaged personal laptop on a public Wi-Fi network, the system can dynamically block the request. The matrix provides the baseline policy, but real-time context is used to make the final call. This adaptive capability is at the heart of a modern Zero Trust Access strategy, transforming your security from a static wall into an intelligent, responsive shield.
Assuming a Breach Has Occurred
A Zero Trust architecture operates under the assumption that a breach isn’t a question of "if" but "when." This mindset forces you to build defences that can limit an attacker's ability to move around your network if they do get inside.
The access control matrix is crucial for this kind of containment. By segmenting access and strictly defining who can talk to what, the matrix creates micro-perimeters around your most critical assets.
Here’s how it helps contain threats:
- Preventing Lateral Movement: If an attacker compromises a user's laptop, they can't use that foothold to jump to a critical server because the matrix explicitly forbids that connection. The user's permissions are locked down to only the resources they absolutely need.
- Isolating Critical Systems: You can use the matrix to create strict rules that isolate sensitive systems, like industrial controllers in an OT environment or financial databases. Only a tiny, predefined set of users or services can communicate with these objects.
- Minimising the Blast Radius: By enforcing least privilege, the matrix ensures that a compromised account has very limited power. This contains the "blast radius" of the attack, preventing a minor incident from snowballing into a catastrophic data breach.
Ultimately, the access control matrix provides the granular, policy-driven control that is essential for bringing the high-level principles of Zero Trust to life. It translates the "never trust, always verify" philosophy into a clear set of enforceable rules that protect your organisation's most valuable assets.
Auditing and Scaling Your Access Control Matrix
Putting together an access control matrix is a huge first step, but it’s definitely not a "set it and forget it" job. If you let it gather dust, your matrix will quickly become outdated and full of holes, creating some serious security gaps. The real trick is building a sustainable governance model that includes regular audits and a smart strategy for scaling the matrix as your organisation grows.
Without that consistent oversight, you open the door to permission creep. This is what happens when users slowly rack up more and more access rights over time, often long after they stop needing them. This quiet accumulation of privileges expands your attack surface bit by bit, leaving sensitive data exposed. A proactive approach to auditing is the only way to keep your matrix in sync with your real-world security needs.
Performing Regular Access Reviews
The cornerstone of keeping your matrix healthy is the periodic access review. Think of this less as a technical chore and more as a crucial business process that confirms everyone’s permissions are still appropriate for their role. The whole point is to systematically enforce the principle of least privilege.
So, what does an access review actually involve?
- Certifying current access: Managers should regularly review and sign off on their team members' permissions, confirming that each one is still genuinely needed for their job.
- Identifying dormant accounts: Be on the lookout for accounts that haven't been used in 90 days or more. These are sitting ducks for attackers and should be disabled or deleted.
- Validating role definitions: If you're using an RBAC model, you need to make sure the permissions assigned to each role still make sense. You don't want them getting bloated with legacy access rights that are no longer relevant.
Regular auditing transforms your access control matrix from a static document into a living, breathing security control. It ensures the rules you defined on day one are still the rules you're enforcing on day 365, preventing those slow-burning security failures.
Strategies for Sustainable Scaling
As your organisation gets bigger, your access control matrix will naturally get more complex. Trying to manage it all by hand quickly becomes a recipe for mistakes and oversights. To scale effectively, you have to lean on automation and well-defined processes.
A solid governance model is particularly important in economically advanced regions where digital infrastructure is deeply woven into every industry. For instance, Singapore's robust economy fuels significant investment in advanced security, where matrix models are essential for managing access across its highly digitalised sectors. The fine-grained control you get from a well-audited matrix is crucial for protecting multi-national operations and critical systems. You can discover more about how economic strength drives security sophistication in ASEAN.
Automated tools can do the heavy lifting by monitoring access logs for unusual activity, flagging excessive permissions, and smoothing out the joiner-mover-leaver (JML) process. By linking your matrix to HR systems, access can be granted and revoked automatically as employees change roles or leave the company. This takes human error out of the equation and guarantees that access rights always match reality.
Answering Your Questions
Even after you've got the basics down, a few questions always pop up when it's time to put an access control matrix into practice. Let's tackle the most common ones to clear up any lingering doubts.
What’s the Main Difference Between an Access Control Matrix and an ACL?
Think of an Access Control List (ACL) as just one column from the bigger matrix. An ACL is like a bouncer's guest list for a single room—it’s attached to one specific resource, like a file, and lists who can get in and what they're allowed to do. It’s all about the object.
The access control matrix, on the other hand, is the master floor plan for the entire building. It gives you the full picture, showing the permissions for all users across all resources in a single, unified view. You see the whole security layout at a glance.
How Does an Access Control Matrix Support Compliance?
An access control matrix is your best friend when it comes to compliance with regulations like GDPR or Singapore's PDPA. It acts as a clear, auditable record showing exactly who has access to what sensitive data and, crucially, why.
This structured format makes it simple for auditors to check if you're actually enforcing security principles like 'least privilege.' A well-kept matrix helps you prove you have deliberate, robust controls in place to protect personal information, which is a non-negotiable for most regulatory standards.
The matrix becomes your single source of truth for access rights. It transforms your security from a messy collection of ad-hoc rules into a defensible, organised framework that can stand up to scrutiny.
Is an Access Control Matrix Still Relevant in the Cloud?
Absolutely. You might be using powerful Identity and Access Management (IAM) tools from cloud giants like AWS or Azure, but the access control matrix is still the strategic blueprint you need before you start clicking around in a cloud console.
The matrix helps you design and visualise a consistent access strategy, which is especially critical in multi-cloud or hybrid setups. It ensures your security rules are coherent everywhere, preventing dangerous gaps or conflicting policies between platforms. In short, you use the matrix to figure out the "what" and "why," then use the cloud provider's tools to handle the "how."
Ready to build a Zero Trust architecture with a modern, dynamic grip on access control? Safous gives you a unified platform that connects identities to applications, providing granular control over privileged access across your entire IT and OT landscape.
Receive the latest news, events, webcasts and special offers!
Share this
You May Also Like
These Related Stories

Blog: Top 5 Benefits of a Zero Trust Architecture

How Zero Trust and Remote PAM Fast-Track ISO/IEC 27001 Compliance



