Managed service providers (MSPs) are critical in safeguarding their clients' sensitive business systems and data. From compromised networks to stolen data and financial losses, the consequences of a cyberattack can be devastating. Unfortunately, cybersecurity threats are on the rise, with 56% of organizations suffering a data breach stemming from malware in 2023.1
Ransomware attacks increased last year, as well. One survey found that 66% of businesses experienced a ransomware attack,2 with the average ransomware payout reaching $1.5 million.3 Given these escalating threats, it's more important than ever for MSPs to guide their clients toward robust security strategies – and zero trust access (ZTA) is at the forefront.
In this blog, we’ll explore how zero trust access stacks up against one of the most popular security solutions, virtual private networks (VPNs), so you can help your clients find the right fit for their unique needs.
What Remote Security Concerns Do MSPs Face?
Modern businesses have fully embraced flexible and remote work arrangements. However, remote access to corporate networks by distributed workforces also introduces significant new security vulnerabilities, including:
Unsecured WiFi Networks
Many remote workers connect to corporate networks using personal or public WiFi, which introduces potential vulnerabilities to be exploited by attackers lurking on unsecured networks.
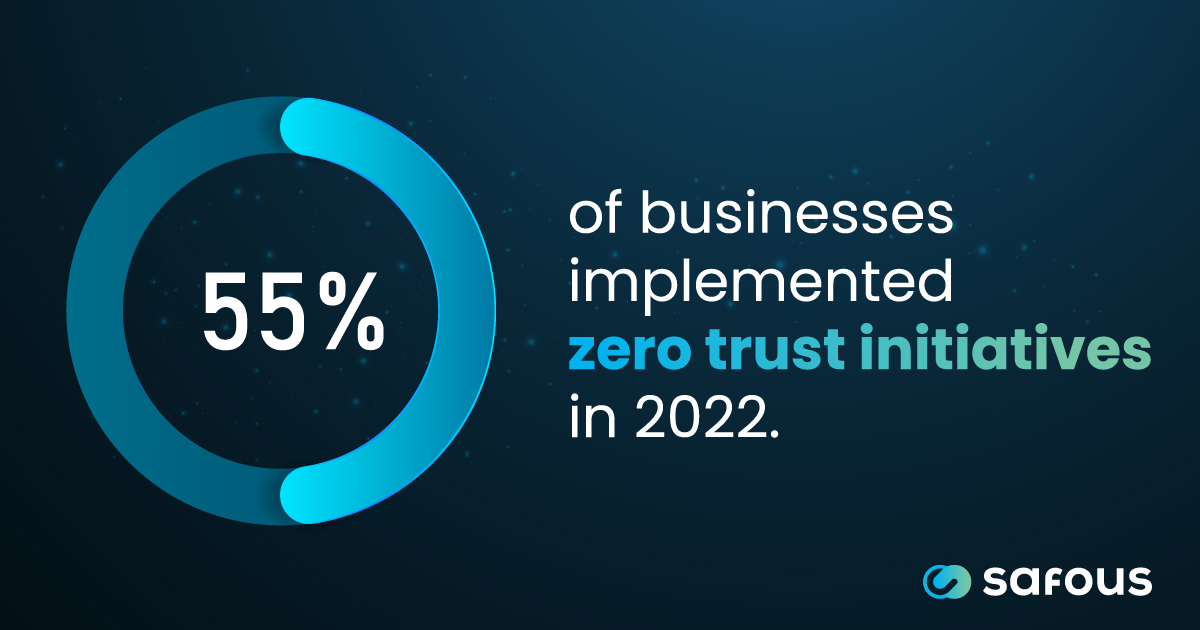
Bring Your Own Device (BYOD) Policies
The rise of BYOD in the workplace has expanded the attack surface, as personal smartphones, tablets, and laptops may not follow strict security protocols and are difficult to monitor centrally. In fact, 55% of remote employees using BYOD devices receive more spam or phishing emails than when working in the office.4
Credential Theft and Account Takeovers
With a growing number of endpoints accessing business networks, there’s a higher risk of criminals obtaining compromised user credentials through techniques like phishing or credential stuffing.

What Is Zero Trust Access?
In today's threat landscape, implicit trust isn't enough. We can no longer assume users, devices, networks, or applications are inherently safe just because they exist within the corporate perimeter. Instead, zero trust operates on "never trust, always verify" and "least privileged access."
A zero trust framework assumes that no user, device, or network can be automatically trusted with unrestricted access. Everything and everyone must be continually authenticated, authorized, and validated before gaining permission to communicate on the network. This comprehensive approach assumes potential compromise and dynamically grants secure access accordingly. Zero trust access enables you to control not only who, but which devices have access to your network.
Here are the main components of a zero trust security approach:
Assume Breach
Zero trust security solutions acknowledge that breaches are inevitable. Since every access attempt represents a potential threat until proven otherwise, no user, device, or network is automatically trusted.
Verify Explicitly
Instead of assuming trust, zero trust requires authentication and authorization before granting access. User identity, device posture, and other factors must be explicitly verified with every request.
Least Privilege Access
The principle of least privilege limits user permissions to only the resources needed for their specific roles, isolating threats and minimizing potential lateral movement and damage if a breach occurs.
Role-Based Access Control
Zero trust access enables businesses to grant access to a user based on their role and the policy-based rights granted to that role. For example, a guest may not be granted certain permissions as compared to an employee.
Network Access Control for Endpoints
Zero trust access ensures that network-connected devices like printers, door access systems, and other "headless" IoT devices are only granted sufficient access to perform a specific function – without unnecessary permissions that create an additional layer of vulnerability on the network.

How Does Zero Trust Access Strengthen Remote Work Security?
Zero trust access uses powerful authentication controls, network segmentation, and least privilege access principles to secure modern work environments. From continuous identity authentication to network segmentation, ZTA solves many remote workforce challenges plaguing organizations today.
ZTA prevents breaches by requiring multi-factor authentication (MFA) whenever a user or device requests network access. Because applications are hidden from the network by default, hackers can’t infiltrate systems or data even with compromised credentials. If an endpoint is infected, network segmentation blocks lateral movement to protect other resources. Plus, centralized security management enables MSPs to enforce uniform access policies and permissions across client sites from a single dashboard.
ZTA delivers all these remote workforce security benefits plus scalability to support growing client networks and evolving regulatory compliance requirements. It modernizes the security of your legacy applications without disrupting business applications – or adding high costs to your cybersecurity budget.
What Is a VPN?
On the other side of the cybersecurity spectrum, we have the virtual private network – an outdated, all-or-nothing access model based on implicit trust. VPNs create encrypted tunnels between end-users and the private corporate network. Authorized individuals receive complete access through the gateway, so they’re free to roam through connected systems and data.
This legacy approach operates under the "secure perimeter" assumption that everything within the network's boundaries can be fully trusted once past the VPN. It fails to account for today's hybrid environments where networks have no fixed boundaries and threats like compromised credentials mean attackers can easily breach unprotected perimeters.

Zero Trust Access vs. VPN: Compared
While VPNs dominated remote access security for decades, the limitations of their implicit trust model have become problematic in today’s IT environments. Here’s how zero trust access vs. VPN solutions stack up:
Security Perimeter
VPNs rely on an outdated assumption of implicit trust within a static security perimeter. Zero trust accounts for hybrid environments with no fixed perimeters by treating all access attempts as potential threats.
Access Policies
VPN access permissions are binary – you're either fully trusted or untrusted. Zero trust dynamically and continuously authenticates identity to enforce granular, adaptive policies based on real-time risk assessment.
Lateral Movement
Once authenticated by a VPN, users typically gain broad access across connected networks. Zero trust isolates threats by strictly granting least privilege access, so each user gets only the permissions needed for each request.
Cloud Performance
VPNs route traffic through gateways, bottlenecking cloud applications. ZTA solutions authenticate users and allow direct-to-cloud access, ensuring remote and in-office employees have fast, secure access to cloud-based apps.
How Can MSPs Support Client Needs With Zero Trust?
Embracing zero-trust security solutions enables MSPs to provide their clients with multiple benefits. First, adopting zero trust can improve your own security posture – a must, as 90% of MSPs suffered a successful cyberattack in 2022.5 Securing your remote access methods helps prevent third-party vendor risks to ensure your customers' sensitive systems and data stay secure.

For clients, zero trust positions MSPs as trusted cybersecurity partners capable of combating advanced threats. By applying least privilege access, continuous risk assessment, and micro-segmentation, you can limit potential attacker movement inside customer networks and gain more control over digital assets thanks to centralized policy management.
Zero trust also allows MSPs to differentiate their offerings and create new revenue streams. More than 60% of businesses are expected to implement zero trust by 2025.6 By positioning your company as a zero-trust expert, you can create new revenue streams while addressing a critical cybersecurity need for your customers.
Zero Trust Access vs. VPN: Find the Best Fit for Your Clients With Safous
Navigating today's cybersecurity challenges requires a balanced approach that secures remote workforces without impacting productivity. MSPs must find security tools that align with flexible, scalable, cloud-centric workflows rather than outdated VPN solutions.
Safous offers MSPs a zero-trust security suite built for modern business environments. Unlike VPN, our platform doesn’t require agent installation – providing your customers with flexibility and lightning-fast onboarding. Safous Zero Trust Access grows alongside your MSP offerings by leveraging modern technology to elevate the security of legacy systems – and offers detailed access controls and audit trail features that aren’t available in other ZTA solutions.
Ready to get started with Safous Zero Trust Access? Request a demo today.
Sources:
- https://www.ptsecurity.com/ww-en/analytics/cybersecurity-threatscape-2023-q3/
- https://assets.sophos.com/X24WTUEQ/at/c949g7693gsnjh9rb9gr8/sophos-state-of-ransomware-2023-wp.pdf
- https://www.varonis.com/blog/cybersecurity-statistics
- https://www.lookout.com/documents/reports/lookout-state-of-remote-work-security-us.pdf
- https://www.msspalert.com/news/90-of-msps-suffer-successful-cyberattacks-n-able-research-finds
Receive the latest news, events, webcasts and special offers!
Share this
You May Also Like
These Related Stories

The MSP’s Blueprint for Zero Trust Access and Compliance

Understanding MSPs’ Role in SME Cybersecurity