Resources
Find all the zero trust resources you need – in one place. Explore our library of blogs, white papers, ebooks, datasheets, and more.
Authentication vs Authorization A Clear Comparison


Authentication vs Authorization A Clear Comparison
Feb 23, 2026
17
min
Demystifying the Cyber Kill Chain
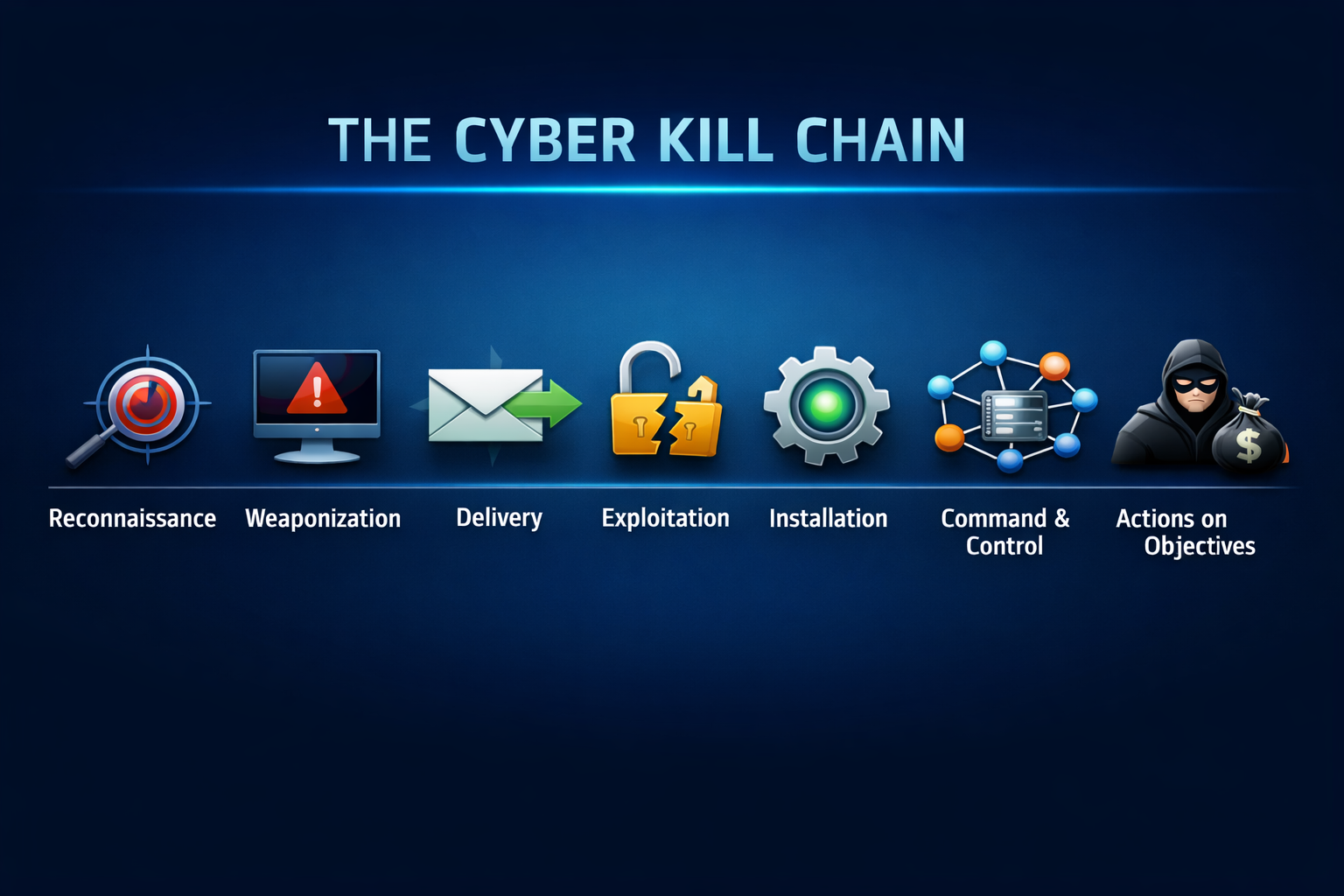

Demystifying the Cyber Kill Chain
Feb 16, 2026
19
min
A Guide to OT Cybersecurity for Critical Infrastructure


A Guide to OT Cybersecurity for Critical Infrastructure
Feb 09, 2026
18
min
Understanding the Access Control Matrix


Understanding the Access Control Matrix
Feb 02, 2026
18
min
8 Ways Legacy Secure Remote Access (SRA) Tools Fall Short in OT Environments
%20Tools%20Fall%20Short%20in%20OT%20Environments/safous-feat-8wayslegacysecureSRA.jpg)
%20Tools%20Fall%20Short%20in%20OT%20Environments/safous-feat-8wayslegacysecureSRA.jpg)
8 Ways Legacy Secure Remote Access (SRA) Tools Fall Short in OT Environments
Jan 15, 2026
5
min
Why SASE Doesn’t Meet OT Security Needs, and What to Do Instead


Why SASE Doesn’t Meet OT Security Needs, and What to Do Instead
Jan 08, 2026
5
min
Why You Need To Know Your Security Posture Before The Holidays Hit


Why You Need To Know Your Security Posture Before The Holidays Hit
Dec 09, 2025
4
min
ASEAN PDPA Compliance and Cybersecurity: A CISO’s Practical Guide


ASEAN PDPA Compliance and Cybersecurity: A CISO’s Practical Guide
Dec 02, 2025
6
min
Why Human-Approved Access Matters for AI-Automated Operations


Why Human-Approved Access Matters for AI-Automated Operations
Nov 26, 2025
5
min
Why Is MFA Essential for Cyber Insurance?


Why Is MFA Essential for Cyber Insurance?
Nov 18, 2025
4
min
Why Identity Governance Needs to Include Human and Machine Users


Why Identity Governance Needs to Include Human and Machine Users
Nov 10, 2025
5
min
From Industry 4.0 to 5.0: Securing Supply Chains in the Human-AI Era


From Industry 4.0 to 5.0: Securing Supply Chains in the Human-AI Era
Oct 28, 2025
5
min


